Cybersecurity


Our Staff Augmentation Models
Onshoring
Our onshoring services connect you with skilled professionals within your region, ensuring real-time collaboration in aligned time zones and cultural settings. This model enables close teamwork and adaptability, ideal for projects requiring quick iteration and high involvement from your in-house team.
Offshoring
Our offshoring solutions provide access to global experts with specialized skills, offering cost efficiency without sacrificing quality. By leveraging offshore resources, we enable round-the-clock productivity across time zones, making it perfect for long-term projects and budget-conscious initiatives.
Nearshoring
Our nearshoring services offer skilled professionals in nearby regions for cost-effective solutions with minimal time zone differences. This model facilitates smooth communication, and frequent collaboration, and is ideal for businesses seeking a regional approach with budget flexibility.
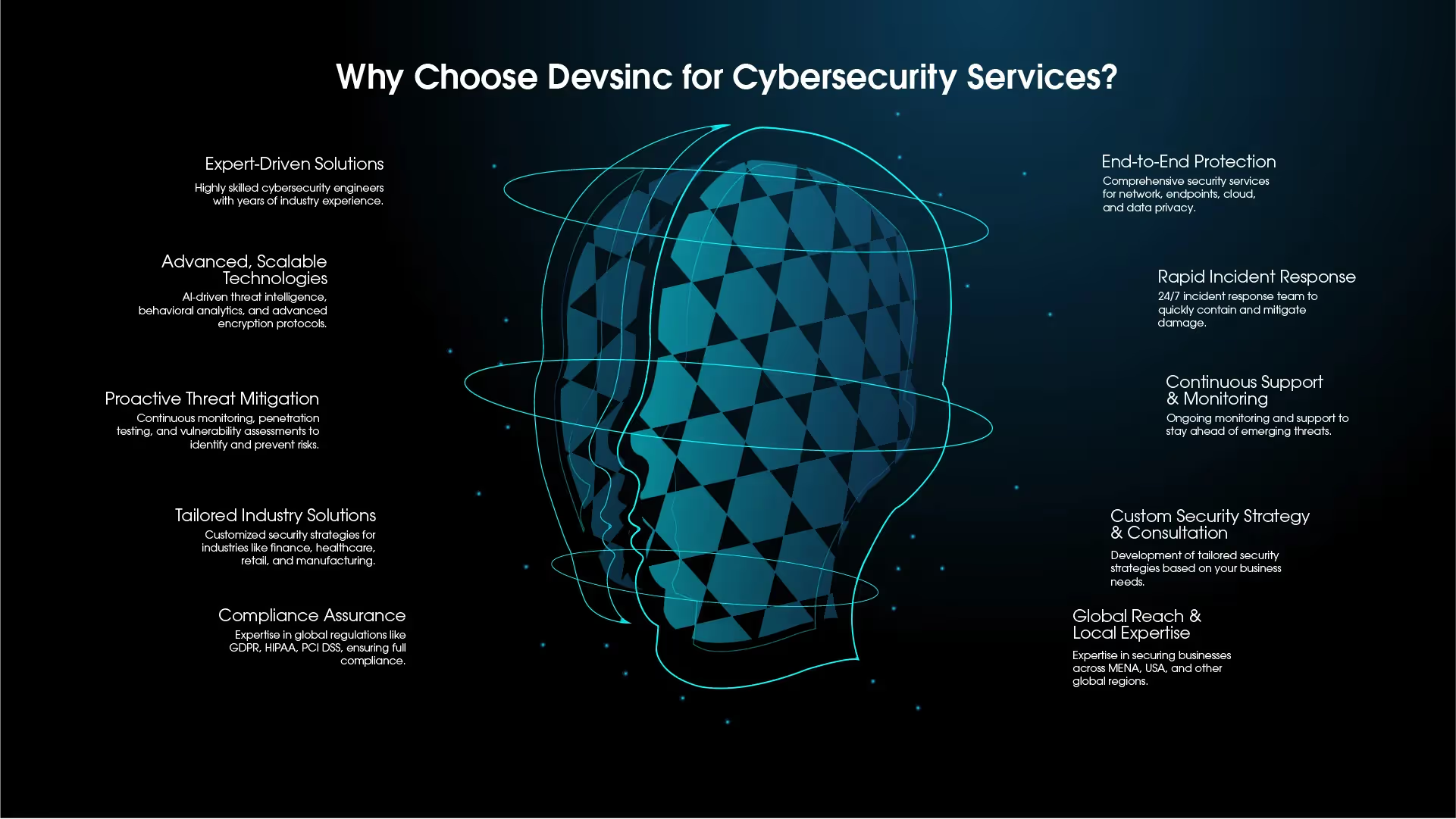
In a digital world where security threats evolve daily, our cybersecurity services provide businesses with a resilient, comprehensive defense strategy. Our engineers employ a robust toolkit, leveraging the latest in threat detection, prevention, and response technologies to create security frameworks that protect your business across all touchpoints. With expertise across network security, cloud security, and endpoint protection, we equip your enterprise with advanced, adaptable defenses that scale with your needs.
What we are good at:
- Threat Detection and Response: Proactive identification and neutralization of threats using AI-powered analytics and real-time monitoring.
- Vulnerability Assessments & Penetration Testing: Rigorous testing and analysis to uncover weaknesses before attackers can.
- Data Protection & Encryption: Advanced encryption and data security protocols to protect sensitive information at rest and in transit.
- Network Security & Firewalls: Implementing firewalls, intrusion prevention systems (IPS), and virtual private networks (VPNs) to secure network traffic.
- Cloud Security Solutions: Securing cloud environments with multi-layered defense strategies, customized access controls, and compliance alignment.
- Endpoint Protection & Device Management: Safeguarding every device connected to your network with advanced endpoint security and monitoring.
- Incident Response & Recovery: Rapid response and disaster recovery planning to minimize downtime and data loss during security events.
- Compliance & Regulatory Support: Ensuring alignment with industry regulations (GDPR, HIPAA, etc.).
- Security Automation & Orchestration: Reducing response times and improving efficiency with automated security workflows.

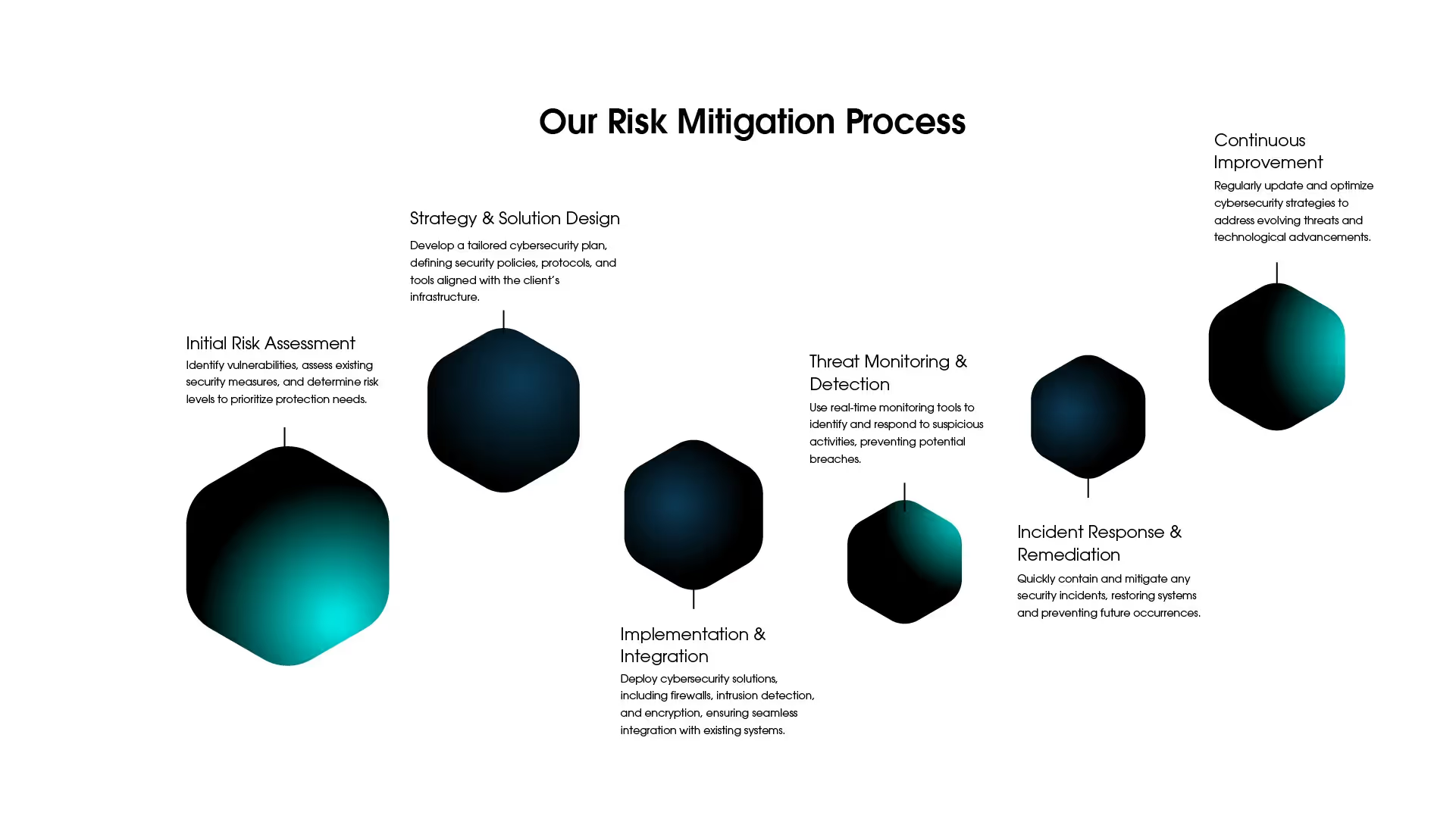
Robust Cyber Defense Services

Vulnerability Assessment & Penetration Testing (VAPT)
Identify system vulnerabilities and conduct controlled attacks to assess system resilience against cyber threats.

Threat Intelligence & Monitoring
Utilize real-time monitoring and analytics to detect, assess, and respond to potential cyber threats proactively.

Incident Response & Recovery
Provide rapid response to cyber incidents with containment, eradication, and recovery to minimize damage and downtime.

Network Security & Firewalls
Implement network security solutions, including advanced firewalls, to protect data flow and prevent unauthorized access.

Endpoint Protection
Secure endpoint devices with antivirus, encryption, and access controls to ensure device and data integrity.

Identity & Access Management (IAM)
Enforce secure user authentication and authorization practices, limiting access based on roles and permissions.
.webp)
Security Information and Event Management (SIEM)
Centralize event logging and monitoring to identify and analyze security incidents in real time.

Data Encryption & Privacy
Protect sensitive data with advanced encryption methods and privacy controls to ensure data security and regulatory compliance.

Cloud Security
Secure cloud environments with encryption, access controls, and monitoring tools, ensuring safe cloud storage and operations.
%20.webp)
Static Application Security Testing (SAST)
Identify vulnerabilities in source code early using advanced tools, ensuring secure coding practices. Integrate seamlessly into CI/CD pipelines for real-time threat detection and mitigation.



We Ensure Security for All Sectors
Telecommunications
Our telecom cybersecurity solutions safeguard network infrastructure, secure customer data, and prevent service disruptions. We provide threat intelligence, secure data transmission, and endpoint protection to maintain reliable and secure communication networks.
Education
We secure educational institutions by protecting student and faculty data, securing online learning platforms, and ensuring data privacy compliance. Our services include firewalls, intrusion detection, and secure access to digital resources to create safe learning environments.
Manufacturing
Our industrial cybersecurity services protect manufacturing lines, intellectual property, and IoT-enabled machinery. We offer network monitoring, access controls, and vulnerability management to safeguard production continuity and prevent operational disruptions.
Energy & Utilities
We secure critical infrastructure with customized cybersecurity solutions for energy providers, including SCADA system protection, network segmentation, and threat intelligence. Our services protect against cyberattacks that could impact power distribution, safety, and reliability.
Retail & E-Commerce
For retail, we deliver secure infrastructure for transaction processing, data encryption, and fraud prevention. Our services ensure PCI compliance, protect customer information, and prevent financial and data theft through continuous monitoring and threat mitigation.
Healthcare
We provide HIPAA-compliant solutions for healthcare, including secure patient data management, real-time monitoring, and rapid incident response. Our services address ransomware risks, securing both electronic medical records and medical IoT devices to protect patient safety and privacy.
Finance & Banking
Our cybersecurity solutions for finance secure transactions, prevent data breaches, and ensure compliance with regulations like PCI DSS and GDPR. We offer fraud detection, secure payment gateways, and data encryption to protect customer trust and financial data integrity.
Government & Public Sector
We help secure government data and operations through solutions that include endpoint security, identity management, and secure cloud adoption. Our services ensure compliance with national standards, protect classified information, and reduce the risk of espionage and cyberattacks.
Our Tech Stack
Equipped with the latest tools, our teams deliver impactful solutions designed to grow your business.












Stories of our transformations across Services and Industries
Explore More






.webp)



Stay One Step Ahead of Cyber Threats
Secure your infrastructure with our end-to-end cybersecurity services.
